Managed Vulnerability Assessment Services
CIS provides fully managed vulnerability assessment services designed to rapidly detect, monitor, and remediate vulnerabilities across both external and internal systems. Our end-to-end solution ensures continuous protection, helping you stay ahead of emerging threats and maintain a strong security posture.
Our Methodology
As cyber threats continue to grow in complexity and frequency, proactively defending your business’s data has never been more critical. Identifying and addressing security weaknesses before attackers can exploit them should be a top priority for any organisation.
Our vulnerability assessment services provide a clear picture of your security posture by uncovering hidden risks and unknown vulnerabilities across your systems. With ongoing support and expert guidance, we help you take immediate action to mitigate threats and strengthen your defences.
Whether used as a standalone service or combined with our broader cybersecurity offerings—such as penetration testing—our assessments form a vital part of a comprehensive and in-depth cyber security strategy tailored to your needs.
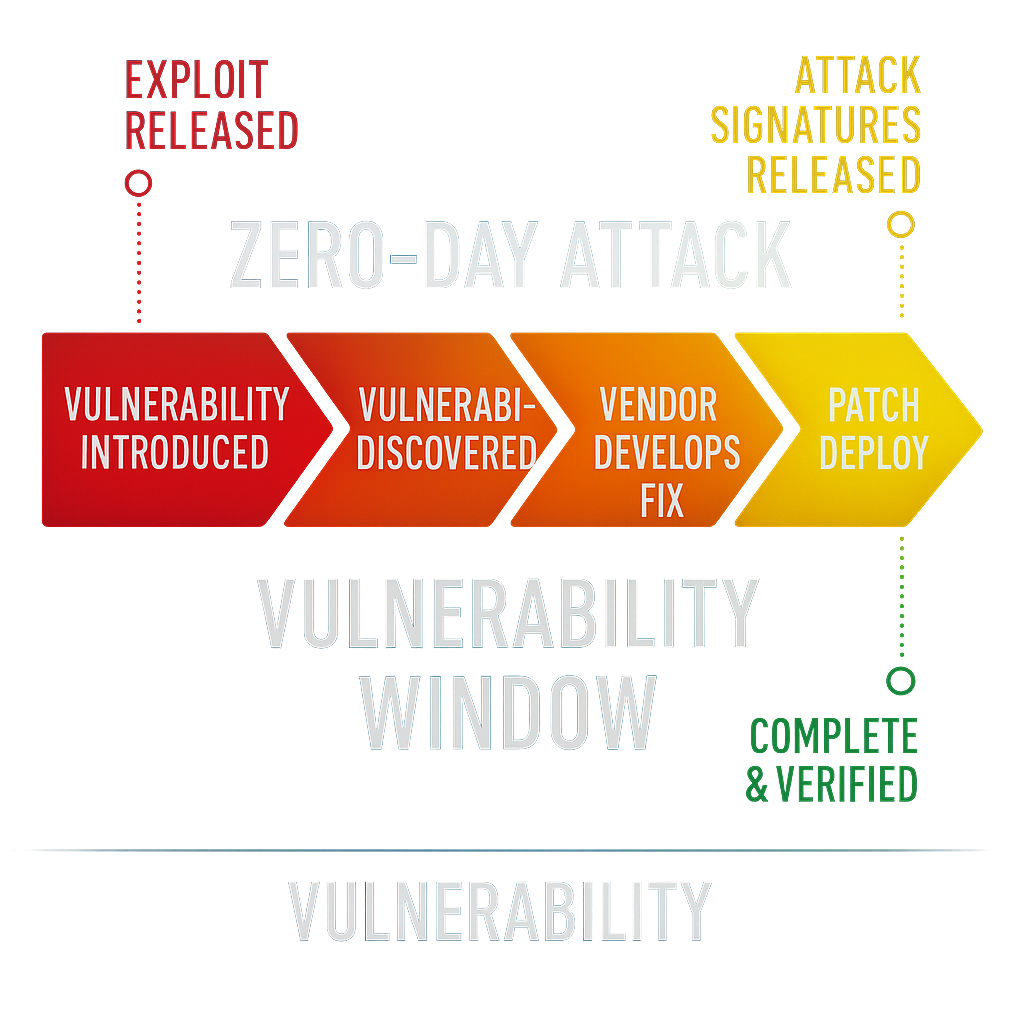
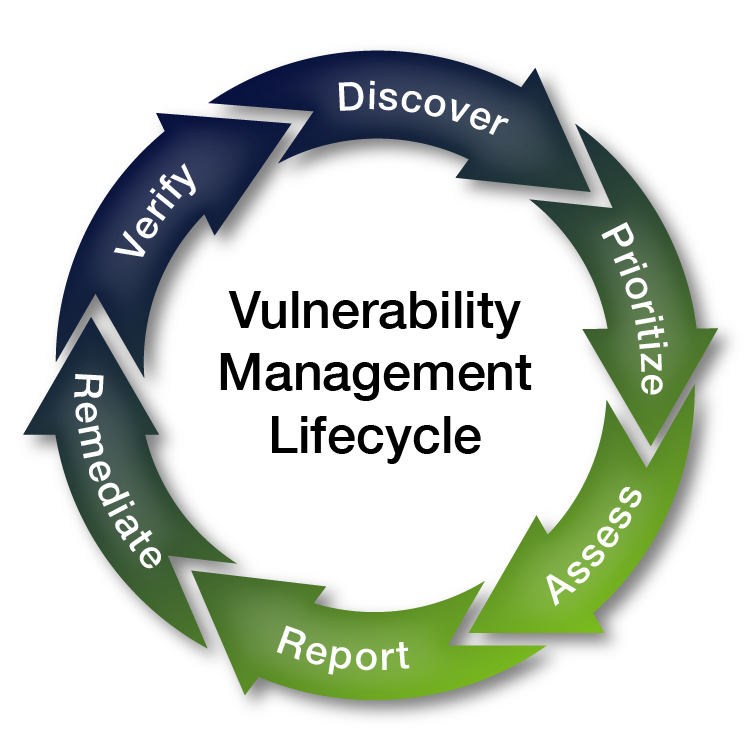
Our Methodology
Our scanning and reporting methodology follows a structured approach to ensure comprehensive vulnerability detection and assessment across your organisation’s IT environment. Qualys utilises its proprietary scanning engine and advanced background tools to deliver an in-depth understanding of security risks. Below is an overview of our methodology:
Scanning Methodology
We leverage Qualys’ industry-leading scanning platform to deliver thorough and accurate vulnerability assessments. The process includes:
- Asset Discovery: Identification of all devices, services, and applications within your network to ensure complete visibility of your IT environment.
- Risk-Based Prioritisation: Categorisation of vulnerabilities based on severity, exploitability, and potential impact, allowing you to focus on critical risks.
- Vulnerability Assessment: Evaluation of systems against a continuously updated database of known vulnerabilities, ensuring the detection of outdated software, vulnerabilities, misconfigurations, and other security risks.
- Actionable Reporting: Comprehensive, prioritised reports with clear remediation guidance to facilitate efficient and effective vulnerability management.
- Continuous Monitoring: Deployment of Qualys cloud agents for near real-time identification of emerging vulnerabilities, ensuring dynamic protection for your IT environment.












Call us on 01223 921 300
Contact us to find out more about our services
Some of the Benefits of vulnerability Assessment include:
Identifies security weaknesses before they can be exploited by attackers, allowing proactive remediation.
Supports ongoing security enhancement through regular assessments and updated threat intelligence.
Minimises the likelihood of successful cyberattacks by uncovering and fixing vulnerabilities across systems.
Gives a detailed view of your attack surface—both internal and external—highlighting hidden or overlooked risks.
Strengthens your overall defences by continuously assessing and addressing security gaps.
Serves as a baseline for deeper testing, allowing pen tests to focus on the most critical areas.
Helps meet standards like ISO 27001, GDPR, PCI-DSS, HIPAA, and others by demonstrating risk management.
Demonstrates your commitment to cybersecurity, reassuring customers, partners, and investors.
Provides clear, actionable insights that guide strategic investment in security tools and policies.
By identifying vulnerabilities early, you reduce the time it takes to respond to potential incidents or breaches.
Get Your Free Security Assessment Sample
Download our free sample Cyber Essentials report to see how we evaluate vulnerabilities, assess risk, and recommend effective security solutions. Just fill out the form to receive instant access. It’s a great way to understand the value we bring in securing your business from digital threats.
You did tell me that no solution would give us 100% protection but knowing that we have your team carrying out regular reviews and available should we ever need them, give me restful night.
I was been told that becoming Cyber Essentials certified was a complex and expensive. Your team made the whole process seam so simple for me. I am not so sure my IT Support company felt the same. Thank you for a first class service.
My and team and I thought our company was too small to ever be a target of a cyber attack but we were clearly wrong! Thank you for helping us and saving our business.
How they trust us?
Why Choose Cyber Essentials Certification?
Protect your business, win more contracts, and show customers you take cybersecurity seriously.
Cyber Essentials
CIS offers Cyber Essentials certification to help your organisation implement essential security measures and protect against common cyber threats.
Vulnerability Management
CIS provides vulnerability management services to identify, assess, and address security weaknesses in your systems, reducing the risk of threats.
Phishing Simulation & User Training
CIS offers comprehensive user training and phishing simulations to improve employee awareness and reduce the risk of falling victim to cyber crime
Managed Detection & Response (MDR)
MDR is a cyber security service that detects, investigates, and responds to threats in real time using advanced monitoring analytics, and expert intervention
