Attack Surface Management: A Key to Cybersecurity Resilience
Discover and secure your organisation’s online attack surface with precise, actionable insights to stay ahead of cyber threats. Our cutting-edge Attack Surface Management (ASM) solution continuously monitors your digital assets, identifying vulnerabilities, misconfigurations, and potential entry points before attackers can exploit them.
Why Attack Surface Management?
In today’s evolving cybersecurity landscape, Attack Surface Management (ASM) is essential for all organisations to proactively identify, assess, and reduce potential entry points that cyber attackers can exploit. An attack surface includes all digital and physical assets that interact with an organisation’s IT infrastructure, such as web applications, APIs, cloud environments, endpoints, and third-party integrations. Without continuous monitoring, security gaps can emerge, increasing the risk of data breaches and cyberattacks.
ASM involves real-time discovery, vulnerability assessment, and remediation strategies to minimise risk exposure. By leveraging automated tools, AI-driven analytics, and continuous penetration testing, businesses can stay ahead of emerging threats. Effective attack surface management not only strengthens cybersecurity defences but also ensures compliance with industry standards like NIST, ISO 27001, and GDPR. As threats evolve, a proactive ASM strategy is crucial to maintaining security resilience and protecting critical assets.
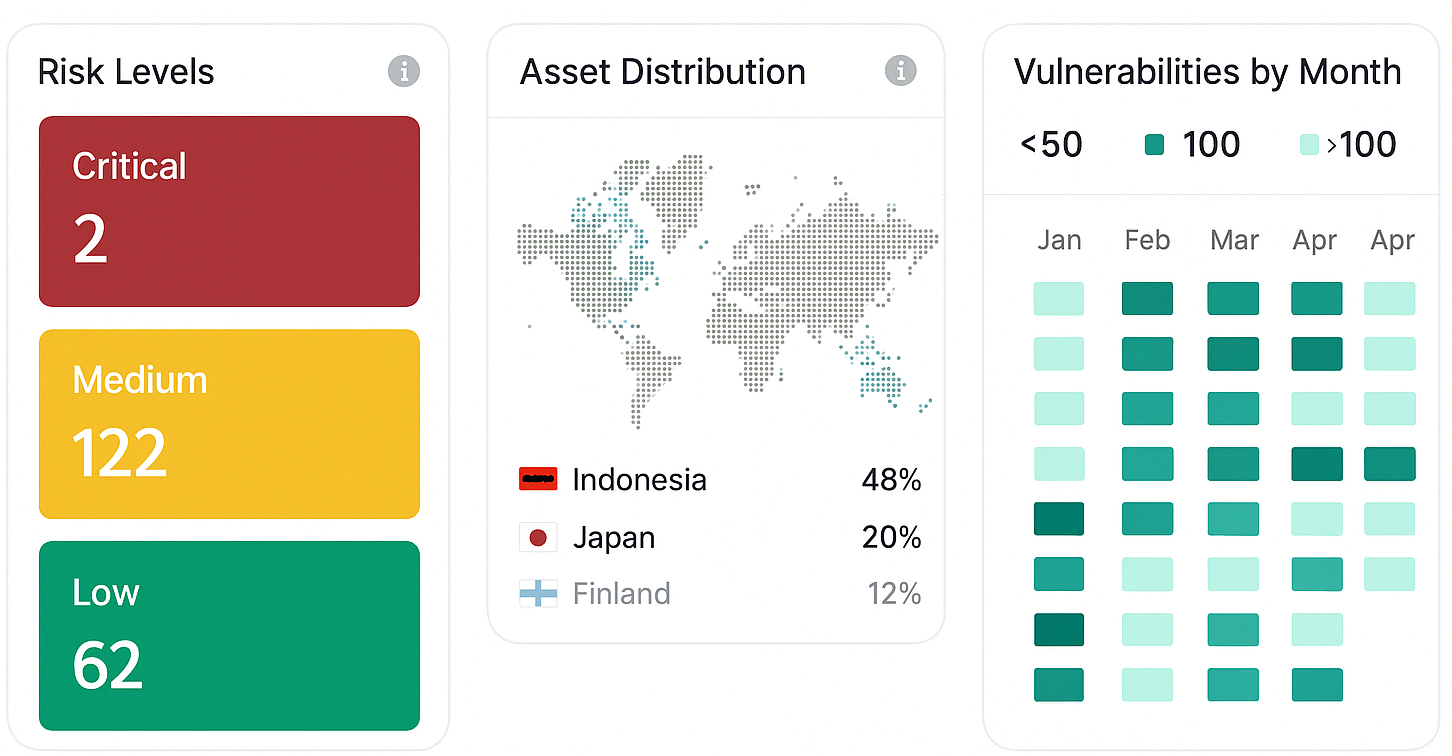
Attack Surface Management As a Service - Pricing
To minimise risk and safeguard your organisation, it’s essential to continuously monitor your domain(s) and promptly address emerging vulnerabilities.
Sign up today to activate your managed continuous monitoring service and stay one step ahead of cyber threats.
No long term commitment
Quarterly Commitment
Annual Commitment
How an attack surface scan could help you

A surface scan reveals vulnerabilities in your attack surface and their associated risks, helping you prevent costly disruptions before they occur.

Gain deep insight into how well potential partners manage cybersecurity and the risks they might introduce to your business. Ensure informed decisions by evaluating their security posture before establishing trust.

Your suppliers’ risks are your risks. Uncover vulnerabilities in your supply chain with a surface scan of both new and existing vendors, ensuring a stronger security posture.
Over 90% of data breaches take under one minute to compromise an entire system!
89 %
Security experts widely believe that AI-driven threats are set to increase significantly in the coming years
70 %
Data breaches have become increasingly common as more information is stored online, with the number of incidents rising by 70% from 2021 to 2024.
61 %
A growing number of leaders fear they aren’t adequately prepared to defend against AI-powered cyberattacks, which are becoming increasingly sophisticated and unpredictable.
How do the CIS ASM Team Work With You?
Working in partnership with you, understanding your business and environment, we will deliver a service that will meet your expectations with:
Dedicated SDM
All our clients are allocated a dedicated Service Delivery Manager as a key point of contact to ensure a smooth partnership and project success.
Expertise and Specialised Knowledge
- Access to highly trained cybersecurity professionals.
- Stay ahead of the latest threats, trends, and technologies.
- Benefit from real-world experience across various industries.
Security Strategy & Roadmapping
- Build a long-term, scalable cybersecurity strategy.
- Align security with business goals and digital transformation efforts.
- Develop incident response plans, disaster recovery, and business continuity.

Get Your Free Security Assessment Sample
Download our free sample Cyber Essentials report to see how we evaluate vulnerabilities, assess risk, and recommend effective security solutions. Just fill out the form to receive instant access. It’s a great way to understand the value we bring in securing your business from digital threats.












You did tell me that no solution would give us 100% protection but knowing that we have your team carrying out regular reviews and available should we ever need them, give me restful night.
I was been told that becoming Cyber Essentials certified was a complex and expensive. Your team made the whole process seam so simple for me. I am not so sure my IT Support company felt the same. Thank you for a first class service.
My and team and I thought our company was too small to ever be a target of a cyber attack but we were clearly wrong! Thank you for helping us and saving our business.
How they trust us?
Why Choose Cyber Essentials Certification?
Protect your business, win more contracts, and show customers you take cybersecurity seriously.
Cyber Essentials
CIS offers Cyber Essentials certification to help your organisation implement essential security measures and protect against common cyber threats.
Vulnerability Management
CIS provides vulnerability management services to identify, assess, and address security weaknesses in your systems, reducing the risk of threats.
Phishing Simulation & User Training
CIS offers comprehensive user training and phishing simulations to improve employee awareness and reduce the risk of falling victim to cyber crime
Managed Detection & Response (MDR)
MDR is a cyber security service that detects, investigates, and responds to threats in real time using advanced monitoring analytics, and expert intervention
